and learn more about how our product can help you.
The SECURITY INCIDENT AND THREAT TRACKING SYSTEM is the right tool for developing and achieving safety successes.
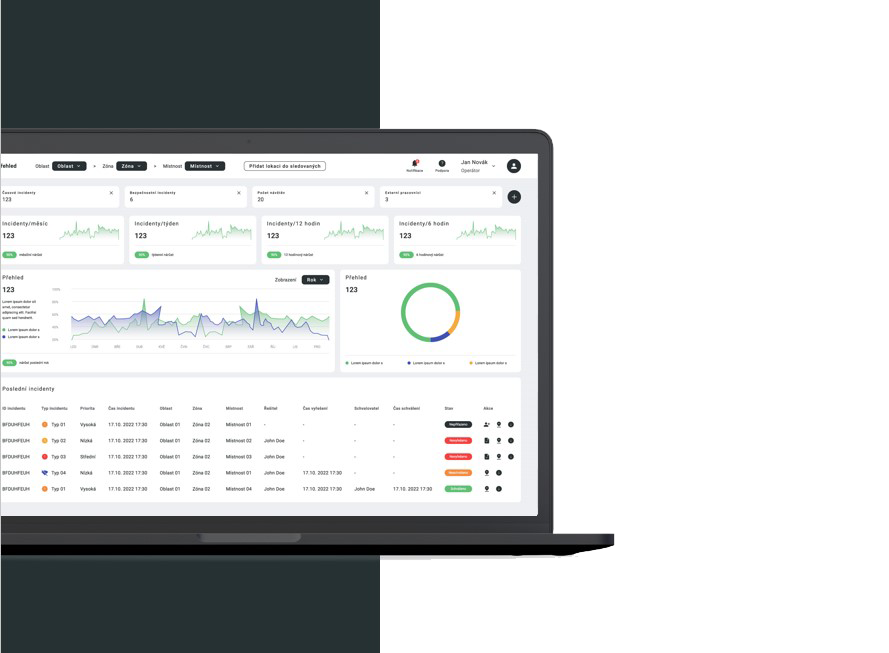
The SECURITY INCIDENT AND THREAT TRACKING SYSTEM App focuses on the detection and evaluation of any event that may be undesirable, hazardous or potentially hazardous in relation to potential damage to property or health of personnel or civilians within the perimeter of the event.
We use the most advanced technology and algorithms to provide the best possible risk analysis and assessment. These analyses allow you to better understand what happened and how you can prevent future incidents.
We know that security is essential to you and your organization. That's why we offer a solution that allows you to better understand security incidents and minimize their risks.
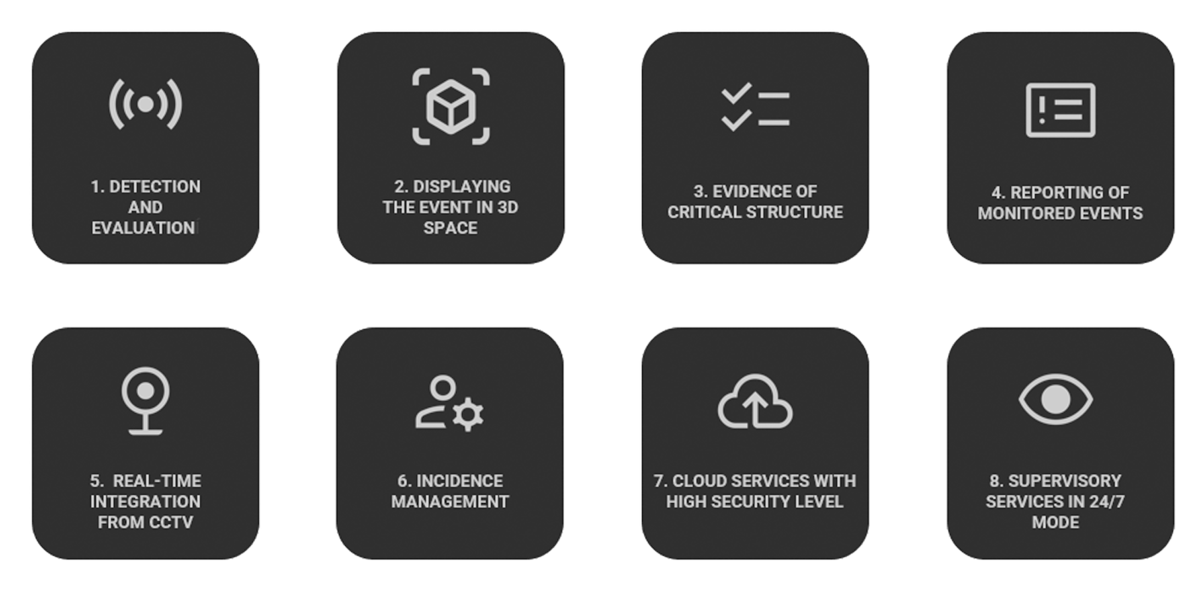
We present to you the functions of the SECURITY INCIDENT AND THREAT TRACKING SYSTEM.
Our functions will make it easier for you to register, manage and evaluate incidents.
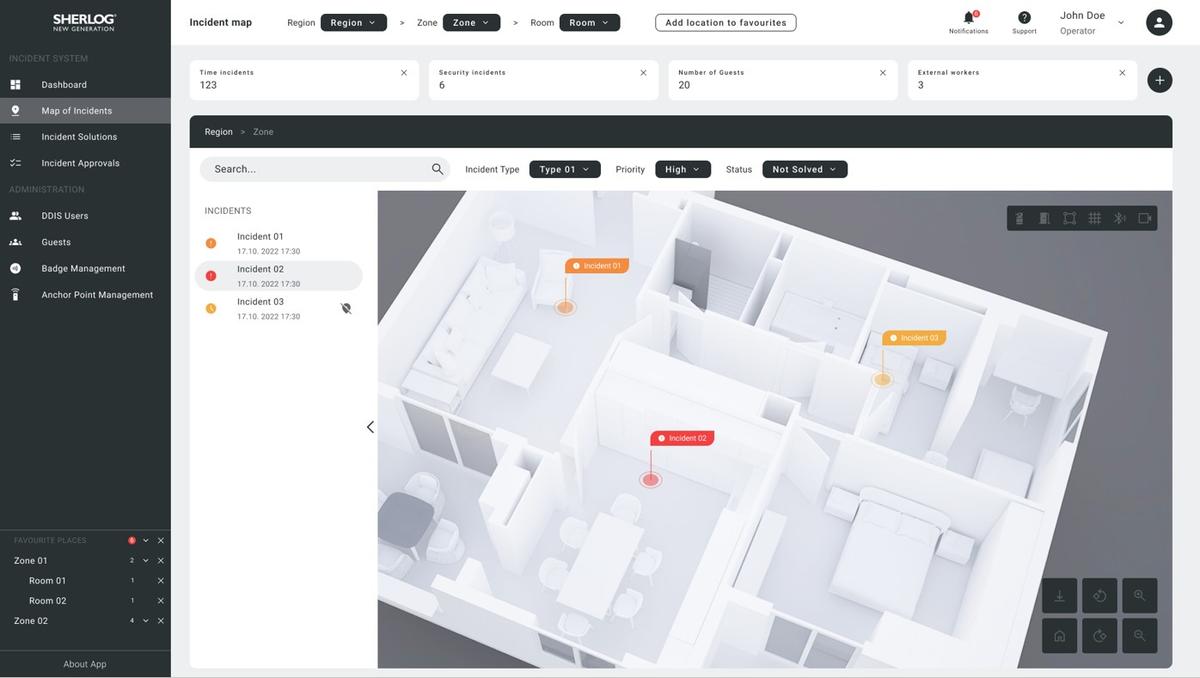
Detection and evaluation allows you to effectively identify and evaluate any security incidents. Because of our cutting-edge technology, your incidents are detected immediately and you have the opportunity to evaluate and solve them as soon as possible.
The incident detection and evaluation feature also allows you to generate information about security incidents and evaluate their impact on your business. You can use this feature to maintain a high level of security and stability of your operation.
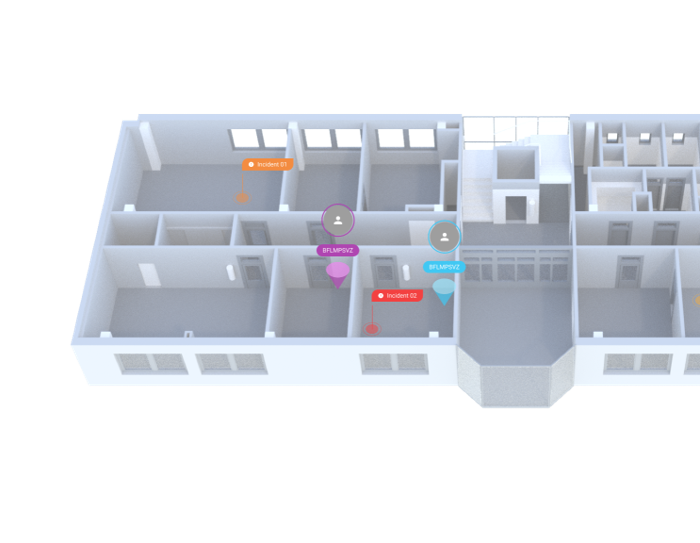
The system offers a unique function of displaying events in an interactive 3D model. However, this model allows users to work with extended functions thanks to the display options, hiding the camera system, critical infrastructure elements, object zones, ratio grid and active elements of the system.
These features allow users to better understand the situation and deal with it effectively.

Our Critical Infrastructure Inventory feature allows you to have precise control over your critical elements. With our feature, you always have an overview of the location of critical elements, which allows you to quickly respond to any incidents and thus ensure the reliable operation, also with our critical infrastructure logging feature, you always have precise control over critical elements, so you can take the right actions to ensure the safety and stability of operations.
Thanks to our function, you can minimize acts of sabotage.
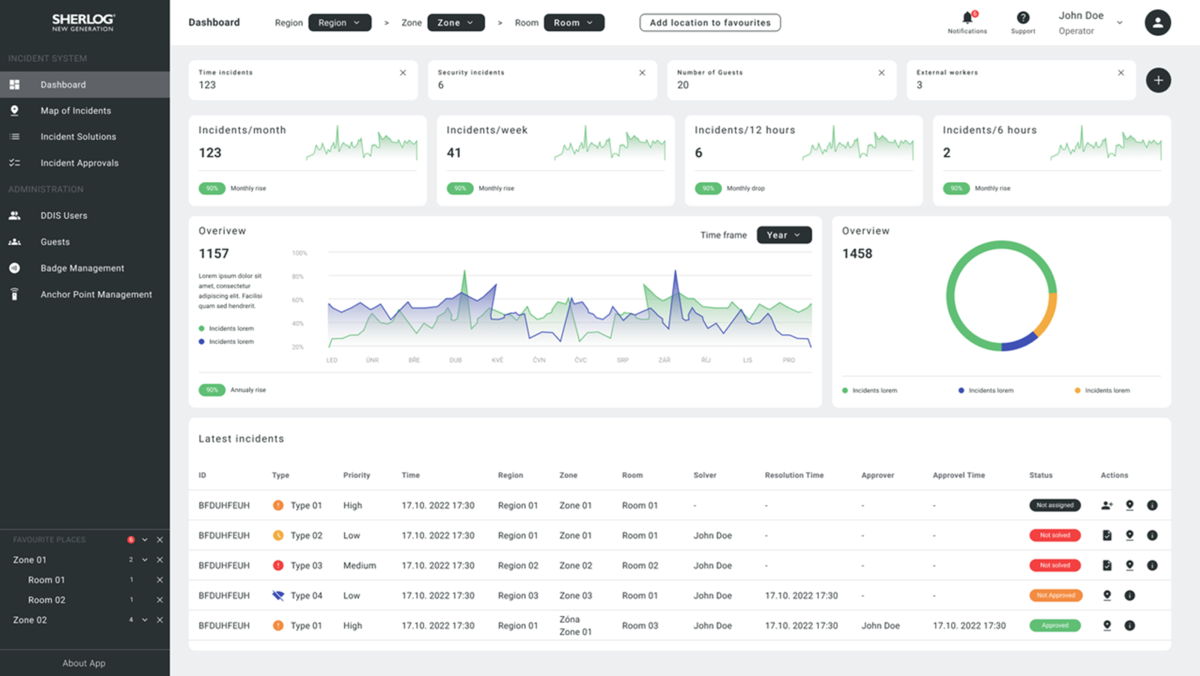
The monitored event reporting feature provides you with powerful security analytics. Thanks to our tools for creating and exporting reports, you have current information on the security situation at your disposal at any time.
These reports allow you to easily identify trends and potential risks. With our outputs, you always have a clear picture of security and can therefore take effective measures.

The application allows you to integrate data from your CCTV systems in real time. You can use this feature to monitor the security of your business and respond quickly to any incidents.
Thanks to our integration of data from CCTV systems, you will always have current information on the security situation and can take quick and effective measures. Get better control over the security of your business with our CCTV data integration.
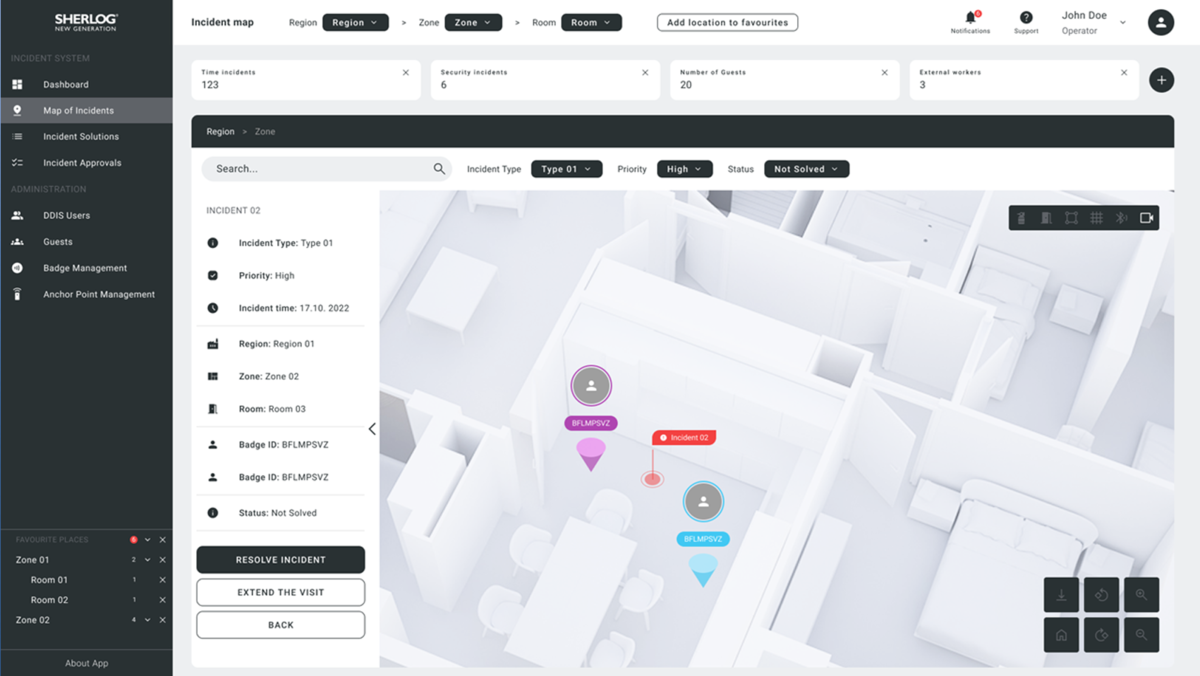
The incident management feature allows you to easily organize and solve incidents. With an intuitive interface and a wide range of incident management tools, you can easily track and resolve any type of incident. Our system also provides powerful analytics so you can see trends and identify potential risks.
Make sure your business is always safe and efficiently managed with our incident management system.

We offer cloud services with the highest level of security to ensure that your data is always safe. With our cloud system, you can be sure that your information is stored in a secure environment with high availability.
Take advantage of our cloud services and ensure a high level of security and reliability for your business.

With our system, you can be sure your operation will be safe 24 hours a day, 7 days a week. With our supervision, you have the opportunity to react immediately to any security incidents and thus ensure the maximum safety of your operation.
With our service, you have professional support and the assurance that your operation will be safe.

and learn more about how our product can help you.
The SECURITY INCIDENT AND THREAT TRACKING SYSTEM is the right tool for developing and achieving safety successes.